GENESIS: A Generalizable, Efficient, and Secure Intra-kernel Privilege Separation (to appear)
Seongman Lee, Seoye Kim, Chihyun Song, Byeongsu Woo, Eunyeong Ahn, Junsu Lee, Yeongjin Jang, Jinsoo Jang, Hojoon Lee, Brent Byunghoon Kang
In Proceedings of the 39th ACM/SIGAPP Symposium On Applied Computing (SAC) 2024
SuM: Efficient shadow stack protection on ARM Cortex-M
Wonwoo Choi, Minjae Seo, Seongman Lee, Brent Byunghoon Kang
Computers & Security 2023 [PDF]
[BIBTEX]
EnclaveVPN: Toward Optimized Utilization of Enclave Page Cache and Practical Performance of Data Plane for Security-Enhanced Cloud VPN
Jaemin Park, Brent Byunghoon Kang
The 26th International Symposium on Research in Attacks, Intrusions and Defenses (RAID) 2023 [PDF]
[BIBTEX]
Towards scalable and configurable simulation for disaggregated architecture
Daegyeong Kim, Wonwoo Choi, Chang-il Lim, Eunjin Kim, Geonwoo Kim, Yongho Song, Junsu Lee, Youngkwang Han, Hojoon Lee, Brent Byunghoon Kang
Simulation Modelling Practice and Theory (SIMPAT) 2023 [PDF]
[BIBTEX]
[SOURCE]
Harnessing the x86 Intermediate Rings for Intra-Process Isolation
Hojoon Lee, Chihyun Song, Brent Byunghoon Kang
IEEE Transactions on Dependable and Secure Computing (TDSC) 2022 [PDF]
[BIBTEX]
3rdParTEE: Securing Third-party IoT Services using the Trusted Execution Environment
Jinsoo Jang, Brent Byunghoon Kang
IEEE Internet of Things Journal 2022 [PDF]
[BIBTEX]
EmuID: Detecting presence of emulation through microarchitectural characteristic on ARM
Yeseul Choi, Yunjong Jeong, Daehee Jang, Brent Byunghoon Kang, Hojoon Lee
Computers & Security 2022 [PDF]
[BIBTEX]
SaVioR: Thwarting Stack-Based Memory Safety Violations by Randomizing Stack Layout
Seongman Lee, Hyeonwoo Kang, Jinsoo Jang, Brent Byunghoon Kang
IEEE Transactions on Dependable and Secure Computing (TDSC) 2021 [PDF]
[BIBTEX]
Agamotto: Accelerating Kernel Driver Fuzzing with Lightweight Virtual Machine Checkpoints
Dokyung Song, Felicitas Hetzelt, Jonghwan Kim, Brent Byunghoon Kang, Jean-Pierre Seifert, Michael Franz
20th USENIX Security Symposium (USENIX Security 2020) [PDF]
[BIBTEX]
AI-HydRa: Advanced Hybrid Approach using Random Forest and Deep Learning for Malware Classification
Suyeon Yoo,Sungjin Kim, Seungjae Kim, Brent Byunghoon Kang
Information Sciences 2020 [PDF]
[BIBTEX]
SelMon: Reinforcing Mobile Device Security with Self-protected Trust Anchor
Jinsoo Jang, Brent Byunghoon Kang
ACM International Conference on Mobile Systems, Applications, and Services. (MobiSys) 2020
[PDF]
[BIBTEX]
Best Paper Honorable Mention
Value-based Constraint Control Flow Integrity
Dongjae Jung, Minsu Kim, Jinsoo Jang, Brent Byunghoon Kang
IEEE Access 2020 [PDF]
[BIBTEX]
The Image Game: Exploit Kit Detection Based on Recursive Convolutional Neural Networks
Suyeon Yoo, Sungjin Kim, Brent Byunghoon Kang
IEEE Access 2020 [PDF]
[BIBTEX]
On the Analysis of Byte-Granularity Heap Randomization
Daehee Jang, Jonghwan Kim, Hojoon Lee, Minjoon Park, Yunjong Jung, Minsu Kim, Brent Byunghoon Kang
IEEE Transactions on Dependable and Secure Computing (TDSC) 2019 [PDF]
[BIBTEX]
Rethinking Anti-Emulation Techniques for Large-Scale Software Deployment
Daehee Jang, Yunjong Jeong, Seongman Lee, Minjoon Park, Kuenhwan Kwak, Donguk Kim, Brent Byunghoon Kang
Computers & Security 2019 [PDF]
[BIBTEX]
POLaR: Per-allocation Object Layout Randomization
Jonghwan Kim, Daehee Jang, Yunjong Jeong, Brent Byunghoon Kang
IEEE/IFIP International Conference on Dependable Systems and Networks (DSN) 2019
[PDF]
[BIBTEX]
Revisiting the ARM Debug Facility for OS Kernel Security
Jinsoo Jang and Brent Byunghoon Kang
Design Automation Conference (DAC) 2019 [PDF]
[BIBTEX]
In-process Memory Isolation Using Hardware Watchpoint
Jinsoo Jang and Brent Byunghoon Kang
Design Automation Conference (DAC) 2019 [PDF]
[BIBTEX]
Securing a communication channel for the trusted execution environment
Jinsoo Jang and Brent Byunghoon Kang
Computers & Security 2019 [PDF] [BIBTEX]
SGX-LEGO: Fine-grained SGX controlled-channel attack and its countermeasure
Deokjin Kim, Daehee Jang, Minjoon Park, Yunjong Jeong, Jonghwan Kim, Seokjin Choi, Brent Byunghoon Kang
Computers & Security 2018
[PDF]
[BIBTEX]
Lord of the x86 Rings: A Portable User Mode Privilege Separation Architecture on x86
Hojoon Lee, Chihyun Song, Brent Byunghoon Kang
Proceedings of the 2018 ACM SIGSAC Conference on Computer and Communications Security (CCS) [PDF] [BIBTEX]
Domain Isolated Kernel: A lightweightsandbox for untrusted kernel extensions
Valentin J.M. Manes, Daehee Jang, Chanho Ryu, Brent Byunghoon Kang
Computers & Security 2018 [PDF] [BIBTEX]
FriSM: Malicious Exploit Kit Detection via a Feature-based String-Similarity Matching
Sungjin Kim, Brent Byunghoon Kang
EAI International Conference on Security and Privacy in Communication Networks (SecureComm 2018)
[PDF]
[BIBTEX]
Malicious URL protection based on attackers' habitual behavioral analysis
Sungjin Kim, Jinkook Kim, Brent Byunghoon Kang
Computers & Security 2018 [PDF] [BIBTEX]
Retrofitting the Partially Privileged Mode for TEE Communication Channel Protection
Jinsoo Jang and Brent Byunghoon Kang
IEEE Transactions on Dependable and Secure Computing (TDSC) 2018 [PDF] [BIBTEX]
A Dynamic Per-context Verification of Kernel Address Integrity from External Monitors
Hojoon Lee, Minsoo Kim, Yunheung Paek, Brent Byunghoon Kang
Computers & Security 2018 [PDF] [BIBTEX]
Domain Isolated Kernel: A lightweight sandbox for untrusted kernel extensions
Valentin J.M. Man`es, Daehee Jang, Chanho Ryu, Brent Byunghoon Kang
Computers & Security 2018 [PDF] [BIBTEX]
Hacking in Darkness: Return-oriented Programming against Secure Enclaves
Jaehyuk Lee, Jinsoo Jang, Yeongjin Jang, Nohyun Kwak, Yeseul Choi, Changho Choi, Taesoo Kim, Marcus Peinado, Brent Byunghoon Kang
17th USENIX Security Symposium (USENIX Security 2017) [PDF] [BIBTEX]
S-OpenSGX: A System-level Platform for Exploring SGX Enclave-Based Computing
Changho Choi, Nohyun Kwak, Jinsoo Jang, Daehee Jang, Kuenwhee Oh, Kyungsoo Kwag, Brent Byunghoon Kang
Computers & Security 2017 [PDF] [BIBTEX]
KI-Mon ARM: A Hardware-assisted Event-triggered Monitoring Platform for Mutable Kernel Object
Hojoon Lee, Hyungon Moon, Ingoo Heo, Daehee Jang, Jinsoo Jang, Kihwan Kim, Yunheung Paek, Brent Byunghoon Kang
IEEE Transactions on Dependable and Secure Computing (TDSC) 2017 [PDF] [BIBTEX]
Invi-server: Reducing the attack surfaces by making protected server invisible on networks
Jaehyun Park, Jiseong Noh, Myungchul Kim, Brent Byunghoon Kang
Computers & Security 2017 [PDF] [BIBTEX]
PrivateZone: Providing a Private Execution Environment using ARM TrustZone
Jinsoo Jang, Changho Choi, Jaehyuk Lee, Nohyun Kwak, Seongman Lee, Yeseul Choi, Brent Byunghoon Kang
IEEE Transactions on Dependable and Secure Computing (TDSC) 2016 [PDF] [BIBTEX]
On-demand Bootstrapping Mechanism for Isolated Cryptographic Operations on Commodity Accelerators
Yonggon Kim, Ohmin Kwon, Jinsoo Jang, Seongwook Jin, Hyeongboo Baek, Brent Byunghoon Kang, Hyunsoo Yoon
Computers & Security 2016 [PDF] [BIBTEX]
OpenSGX: An Open Platform for SGX Research
Prerit Jain, Soham Desai, Seongmin Kim, Ming-Wei Shih,
JaeHyuk Lee, Changho Choi, Young Shin, Taesoo Kim, Brent Byunghoon Kang, Dongsu Han
23nd Annual Network and Distributed System Security Symposium, NDSS 2016 (15.4%) [PDF] [BIBTEX]
Vulnerabilities of network OS and mitigation with state-based permission system
Jiseong Noh, Seunghyeo Lee, Jaehyun Park, Seungwon Shin, and Brent Byunghoon Kang
Security and Communication Networks 2015 [PDF] [BIBTEX]
Detecting and Preventing Kernel Rootkit Attacks with Bus Snooping
Hyungon Moon, Hojoon Lee, Ingoo Heo, Kihwan Kim, Yunheung Paek and Brent Byunghoon Kang
IEEE Transactions on Dependable and Secure Computing [PDF] [BIBTEX]
Implementing an Application Specific Instruction-set Processor for System Level Dynamic Program Analysis Engines
Ingoo Heo, Minsoo Kim, Yongje Lee, Changho Choi, Jinyong Lee, Brent Byunghoon Kang, and Yunheung Paek
ACM Transactions on Design Automation of Electronic Systems [PDF] [BIBTEX]
Efficient Kernel Integrity Monitor Design for Commodity Mobile Application Processors
Ingoo Heo, Daehee Jang, Hyunggon Moon, Hansu Cho, Seungwook Lee, Brent Byunghoon Kang, and Yunheung Paek
Journal of Semiconductor Technology and Science [PDF] [BIBTEX]
SeCReT: Secure Channel between Rich Execution Environment and Trusted Execution Environment
Jinsoo Jang, Sunjune Kong, Minsoo Kim, Daegyeong Kim and Brent Byunghoon Kang
22nd Annual Network and Distributed System Security Symposium, NDSS 2015 (Acceptance rate 16.6% (50/302)) [PDF] [BIBTEX] [PRESENTATION]
ATRA: Address Translation Redirection Attack against Hardware-based External Monitors
Daehee Jang, Hojoon Lee, Minsoo Kim, Daehyeok Kim, Daegyeong Kim and Brent Byunghoon Kang
Proceedings of the 2014 ACM SIGSAC Conference on Computer and Communications Security (CCS) (Acceptance rate 19.5% (114/585)) [PDF] [BIBTEX] [PRESENTATION]
Rosemary: A Robust, Secure, and High-performance Network Operating System
Seungwon Shin, Yongsoo Song, Taekyung Lee, Sangho Lee, Jaewoong Chung, Phillip Porras, Vinod Yegneswaran†, Jiseong Noh and Brent Byunghoon Kang
Proceedings of the 2014 ACM SIGSAC Conference on Computer and Communications Security (CCS) (Acceptance rate 19.5% (114/585)) [PDF] [BIBTEX]
KI-Mon: A Hardware-assisted Event-triggered Monitoring Platform for Mutable Kernel Object
Hojoon Lee, Hyungon Moon, Daehee Jang, Kihwan Kim, Jihoon Lee, Yunheung Paek and Brent Byunghoon Kang
13th USENIX Security Symposium (USENIX Security 2013) (Acceptance rate: 15.9% (44/277)) [PDF] [BIBTEX]
Vigilare: Toward Snoop-based Kernel Integrity Monitor.
Hyungon Moon, Hojoon Lee, Jihoon Lee, Kihwan Kim, Yunheung Paek and Brent Byunghoon Kang
Proceedings of the 2012 ACM SIGSAC Conference on Computer and Communications Security (CCS) (Acceptance rates: 17.2%, 14%, 18.9%) [PDF] [BIBTEX]
DoubleGuard: Detecting Intrusions In Multi-tier Web Applications.
M. Le, A. Stavrou, B. Kang
IEEE Transactions on Dependable and Secure Computing, July-Aug. 2012, Volume: 9, Issue: 4 Page(s): 512-525.
[PDF] [BIBTEX]
Identifying Users with Application-Specific Command Streams
A. El-Masri, P. Likarish, H. Wechsler, B. Kang
Twelfth Annual International Conference on Privacy, Security and Trust (PST 2014) July 2014, REGULAR paper. (Acceptance rate 47/161 = 29%) [PDF] [BIBTEX]
Developing and Refining Infected-Host Enumeration Methods for Advanced Botnets
C. Nunnery and B. Kang
2012.12.25, Telecommunications Review, Vol. 22 Issue 6.
Entropy-Based Measurement of IP Address Inflation in the Waledac Botnet.
R. Weaver, C. Nunnery, G. Singaraju, and B. Kang
CERT FloCon 2011
Towards Complete Node Enumeration in a Peer-to-Peer Botnet.
B. Kang, E. Chan-Tin, C. Lee, J. Tyra, H. Kang, C. Nunnery, Z. Wadler, G. Sinclair, N. Hopper, D. Dagon and Y. Kim
ACM Symposium on Information, Computer & Communication Security (ASIACCS 2009) [PDF] [BIBTEX]
Hash History Approach for Reconciling Mutual Inconsistency
B. Kang, R. Wilensky, J. Kubiatowicz, Proceedings of 23rd International Conference on Distributed Computing Systems (ICDCS), 2003 (Acceptance rates: 17.7%, 17.7%, 13.8%)
[PDF] [BIBTEX]
Network Support for Mobile Multimedia using a Self-adaptive Distributed Proxy
Z. Mao, H. So, B. Kang and R. Katz
Proceedings of 11th International Workshop on Network and Operating Systems Support for Digital Audio and Video (NOSSDAV), 2001 (Acceptance rates: 33.3%, 30.5%, 30%)
[PDF] [BIBTEX]
Toward a Model of Self-administering Data
B. Kang and R. Wilensky
Proceedings of the first ACM/IEEE-CS Joint Conference on Digital Libraries (JCDL), 2001 (Acceptance rates: 30%, 25%, 33%)
[PDF] [BIBTEX]
Dissertation: “S2D2: A Framework for Scalable and Secure Optimistic Replication.”
B. Kang
Ph.D. Dissertation, 2004. UC Berkeley TechReport, UCB/CSD-04-1351, Committee: Robert Wilensky, John Kubiatowicz, Eric Brewer, and John Chuang Qualification Exam Area: Operating Systems (with Security) [PDF]
Utility Patent: "SYSTEM AND METHOD FOR IMPLEMENTING A HIDDEN SERVER".
Filed by George Mason University, January 12, 2012.
Sole Inventor, Publication number: US 2012/0180127, Publication date: July 12, 2012
Entropy-Based Measurement of IP Address Inflation in the Waledac Botnet
R. Weaver, C. Nunnery, G. Singaraju, and B. Kang, CERT/CC (Computer Emergency Readiness Team) Proceedings of FloCon 2011. [PDF]
Tumbling Down the Rabbit Hole: Exploring the Idiosyncrasies of Botmaster Systems in a Multi-Tier Botnet Infrastructure.
C. Nunnery, G. Sinclair and B. Kang
USENIX LEET 2010 [PDF]
The Waledac Protocol: The How and Why.
G. Sinclair, C. Nunnery and B. Kang
IEEE Malware 2009 [PDF]
Tracking Email Reputation for Authenticated Sender Identities.
G. Singaraju, J. Moss and B. Kang
CEAS 2008 [PDF]
Concord: A Secure Mobile Data Authorization Framework for Regulatory Compliance.
G. Singaraju and B. Kang
LISA 2008 [PDF]
RepuScore: Collaborative Reputation Management Framework for Email Infrastructure.
G. Singaraju and B. Kang
LISA 2007 [PDF]
Peer-to-Peer Botnets: Overview and Case Study.
J. Grizzard, V. Sharma, C. Nunnery, B. Kang and D. Dagon.
(Cited by 340 times since its publication in Fall 2007)
USENIX HOTBOTS 2007 [PDF]
Privilege Messaging: An Authorization Framework over Email Infrastructure
B. Kang , G. Singaraju, and S. Jain
USENIX 20th Large Installation System Administration Conference (USENIX LISA), 2006 [PDF]
RegColl: Centralized Registry Framework for Infrastructure System Management
B. Kang, V. Sharma, and P. Thanki
USENIX 19th Large Installation System Administration Conference (USENIX LISA), 2005 [PDF]
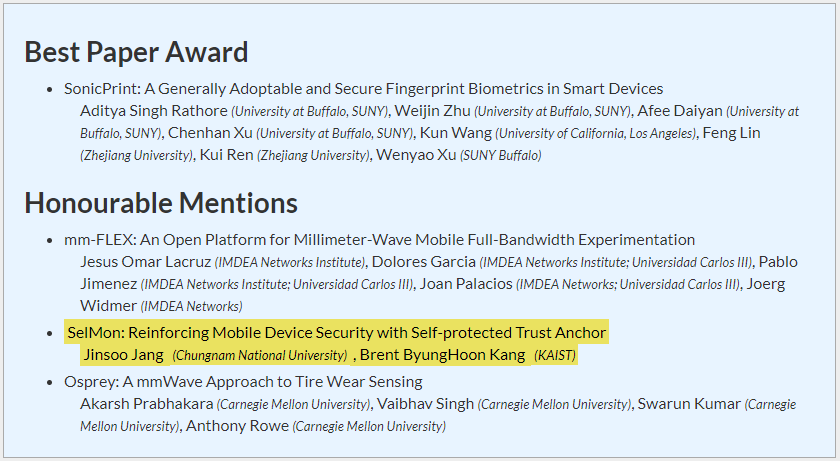 Prof. Jinsoo Jang and Prof. Brent Byunghoon Kang's collaborative team earned the "Best Paper Honourable Mention" from MobiSys 2020.
Prof. Jinsoo Jang and Prof. Brent Byunghoon Kang's collaborative team earned the "Best Paper Honourable Mention" from MobiSys 2020.  The CyberSecurity@KAIST International Workshop June 9(Sat), 2018, KAIST N1 building #102, Daejeon, Korea
The CyberSecurity@KAIST International Workshop June 9(Sat), 2018, KAIST N1 building #102, Daejeon, Korea The 19th World Conference on Information Security Applications August 23-25, 2018, Lotte City Hotel, Jeju Island, Korea
The 19th World Conference on Information Security Applications August 23-25, 2018, Lotte City Hotel, Jeju Island, Korea Daehee Jang won the prize money of 5 million won in his paper(RUMA: Rethinking Byte Granularity Heap Randomization) and took second place in the hacking defense contest which was held together.
Daehee Jang won the prize money of 5 million won in his paper(RUMA: Rethinking Byte Granularity Heap Randomization) and took second place in the hacking defense contest which was held together.  KI-MON and VIGILARE are new hardware-based security monitors designed to defend against OS rootkit attacks, however the recent discovery of “Address Translation Redirection Attack (ATRA)” calls for more robust monitor designs that can overcome the fundamental architectural limitation.
KI-MON and VIGILARE are new hardware-based security monitors designed to defend against OS rootkit attacks, however the recent discovery of “Address Translation Redirection Attack (ATRA)” calls for more robust monitor designs that can overcome the fundamental architectural limitation. pwnable.kr is a Wargame site which provides various challenges regarding educational system exploitation. CySecLab is running the pwnable.kr server which is created by one of our student.
pwnable.kr is a Wargame site which provides various challenges regarding educational system exploitation. CySecLab is running the pwnable.kr server which is created by one of our student. Four of the CySecLab members (PwnPineappleApplePwn) participated SECCON2016 International CTF competition and awarded 2nd place.
Four of the CySecLab members (PwnPineappleApplePwn) participated SECCON2016 International CTF competition and awarded 2nd place.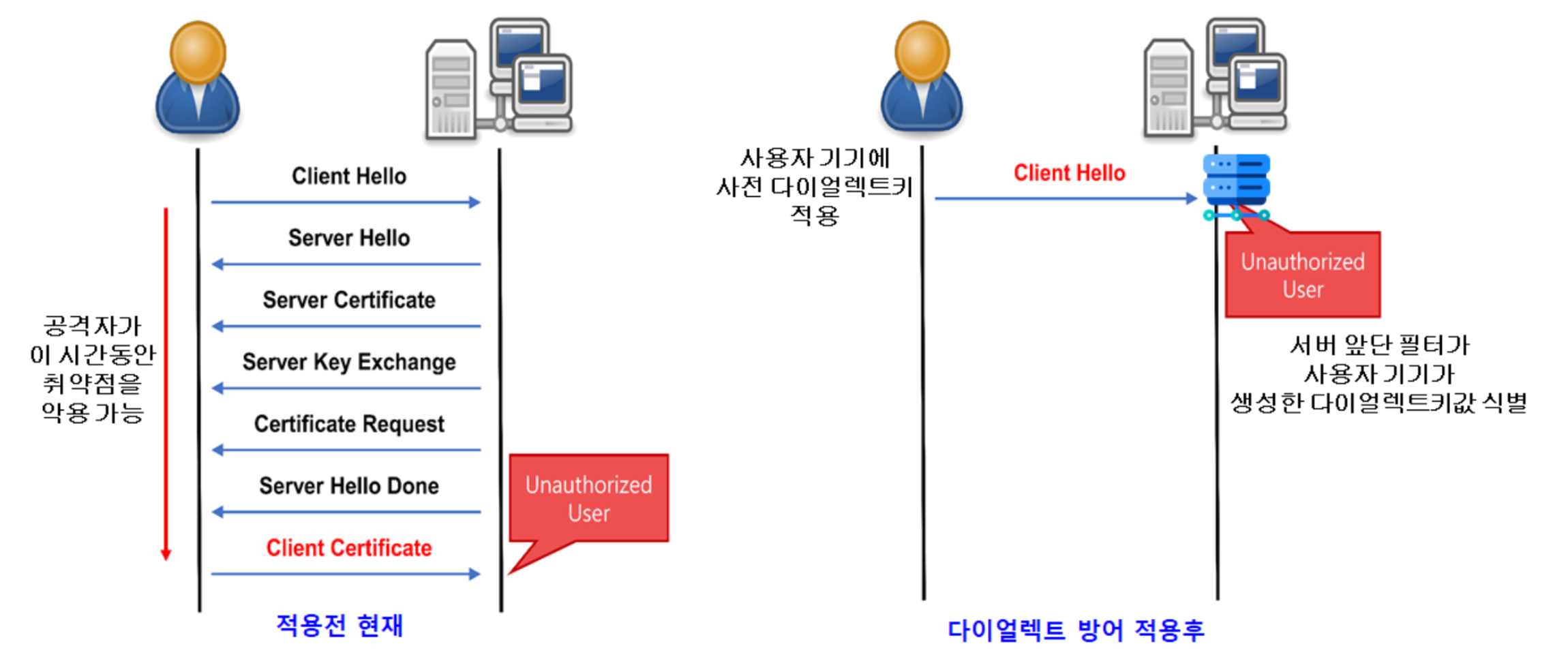 The protocol dialect technique is covered by the media
The protocol dialect technique is covered by the media


























